 NebuAd is a highly controversial behavioral targeted advertising system implemented by many leading ISP's, the sophisticated deep-packet inspection appliance based system at your ISP level analyzes customer's websurfing habits delivering micro-targeted advertising to them, the overall approach used to intercept, analyze and alter the visited webpage's html makes it no less then a Spyware and is raising substantial privacy questions.
NebuAd is a highly controversial behavioral targeted advertising system implemented by many leading ISP's, the sophisticated deep-packet inspection appliance based system at your ISP level analyzes customer's websurfing habits delivering micro-targeted advertising to them, the overall approach used to intercept, analyze and alter the visited webpage's html makes it no less then a Spyware and is raising substantial privacy questions.
In a new investigatory report, the author Robert M. Topolski found that NebuAd uses TCP/IP packet monitoring that “monitors, intercepts and modifies the contents of Internet packets” as consumers surf online, the report also provide details how NebuAd is intercepting web-traffic and inserting javascript codes into webpages:
"Upon reviewing the record of TCP packets from Google’s server, it is observable that that an extra packet appears in the data stream before the data stream closes. The contents of
this added packet are added to the code underlying Google’s Web page. The added packet
contains JavaScript code that causes a Web browser to visit another site. Evidence (see
below) indicates that this packet is a forgery and did not come from Google, but from
some other point within the network."
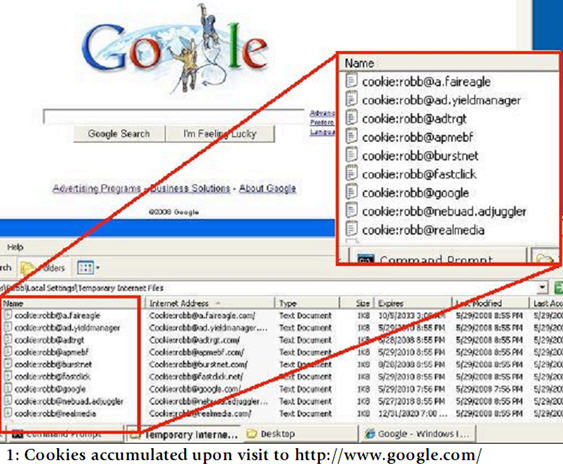
Some critics are also concerned about NebuAd superimposing its own advertising over the ads of other advertisers killing site owners revenue, or placing additional advertising to page. The substance to these concerns can likely be traced to the company's "Fair Eagle" operation, patent application data that mention such inventions, and a loose relationship to Claria Corporation whose products and history suggest such tactics.
View Report : NebuAd and Partner ISPs: Wiretapping, Forgery and Browser Hijacking
Add new comment