 There is no doubt that cyber spying is the most preferred new age intelligence gathering tactic used by almost all countries, but countries like USA and China have already been exposed for using technology as a weapon.
There is no doubt that cyber spying is the most preferred new age intelligence gathering tactic used by almost all countries, but countries like USA and China have already been exposed for using technology as a weapon.
The conclusive proof's fingering all leads to an Isarel, American joint-venture targeting Iranian nuclear facilities using the world's most advanced computer malware Stuxnet are now well known publicly. To make things even more interesting researchers at Kaspersky Labs have now unveiled another extraordinary peace of cyber-weapon, named "Flame" the data-mining malware has already caused substantial damage and massive amounts of data loss as admitted by Iranian officials. Iranian authorities are also claiming that the virus damaged centrifuges operating at its uranium enrichment facility at Nantaz and gathered data of its oil fields by breaching into computers of high-ranking officials.
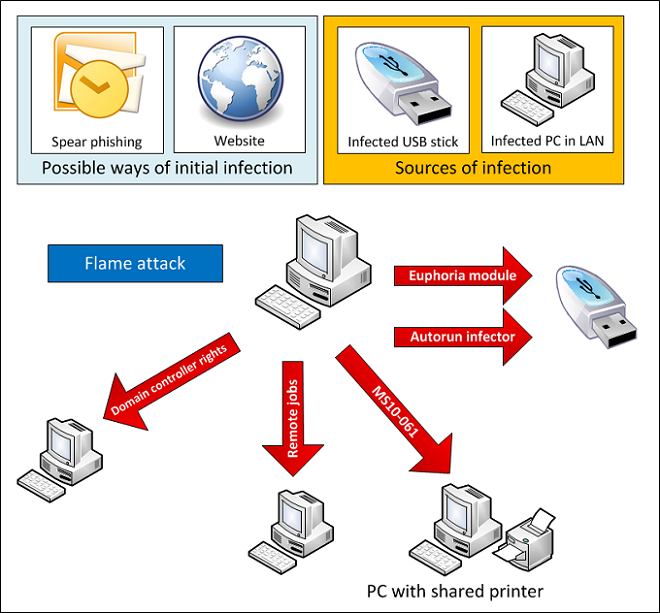
Due to the complex and very sophisticated technology (20 MB in total) used by this malware it has been labelled "the most sophisticated cyber weapon yet unleashed". The ‘Flame’ cyber espionage worm is highly modular in nature and is specifically targeted at middle-east countries, the sophisticated attack toolkit with similarities to Stuxnet and Duqu malware's is basically a combination of computer backdoor, Trojan, and a worm. The success of this weapon can be gauged from the fact that it is believed to be spying since past 5 years undetected. The sophistication can be measured by the fact that "Flame" has 80 known Command-N-Control servers dedicated to itself and the modular nature of the malware allows its controllers to load/unload code of there choice anytime.