 Hacking is an art and can be used for both offense and defense, for pro-active defense you need to know hacker tactics for securing yourself/organization against hacking, there exists a very thin line of hacker ethics distinguishing between a WhiteHat and a BlackHat hacker, I have always been very curious in learning this dark art for ethical purpose and finally got hold of "The Secret Of Hacking" - Ethical hacking course, unlike other outdated ebooks and basic courses this one is authored by an established Government recognized Indian security company and really packs a punch with all aspects of hacking and securing as promised on the sales page.
Hacking is an art and can be used for both offense and defense, for pro-active defense you need to know hacker tactics for securing yourself/organization against hacking, there exists a very thin line of hacker ethics distinguishing between a WhiteHat and a BlackHat hacker, I have always been very curious in learning this dark art for ethical purpose and finally got hold of "The Secret Of Hacking" - Ethical hacking course, unlike other outdated ebooks and basic courses this one is authored by an established Government recognized Indian security company and really packs a punch with all aspects of hacking and securing as promised on the sales page.
The course comes with one printed book and two DVD's having more then 14500 security related tools and 200+ Hacking E-books/Videos, the best part is that you get a lifetime membership with access to an ever growing collection of videos and technical support.
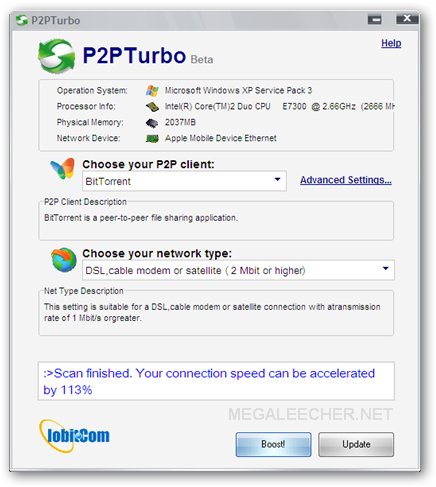
 This years BlackHat security conference revealed some serious security loophole in way SSL certificates can be made to spoof domain identity, the trick allows phishers to spoof and display certificate of their choice on user browsers, this means that the attacker could make you land onto a phishing domain (say
This years BlackHat security conference revealed some serious security loophole in way SSL certificates can be made to spoof domain identity, the trick allows phishers to spoof and display certificate of their choice on user browsers, this means that the attacker could make you land onto a phishing domain (say  In somewhat major blow to anti-piracy efforts Microsoft Windows 7 Ultimate activation crack is now available before the official release of the software, the OEM SLP Master Product Key based activation crack completely bypasses the Windows Genuine Advantage validation allowing users a fully functional unlocked copy of the operating-system, the crack was made possible by extracting the OEM certificate and key from .wim files contained in leaked Windows 7 Ultimate OEM DVD ISO from Lenovo.
In somewhat major blow to anti-piracy efforts Microsoft Windows 7 Ultimate activation crack is now available before the official release of the software, the OEM SLP Master Product Key based activation crack completely bypasses the Windows Genuine Advantage validation allowing users a fully functional unlocked copy of the operating-system, the crack was made possible by extracting the OEM certificate and key from .wim files contained in leaked Windows 7 Ultimate OEM DVD ISO from Lenovo.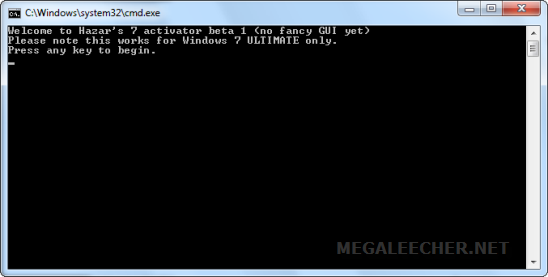
 Similar to the
Similar to the 
 All network adapters have an unique identifier assigned by the manufacturer known as Media Access Control address (MAC address), this MAC address is used to identify a particular device on a network and was intended as a globally unique identification numbering system to trace network activity and implement restrictions and security, MAC address are used by many ISP's worldover for binding network access to a particular modem, however this MAC number can be changed easily via readily available noob friendly MAC spoofing tools, here are few tricks and tools to spoof your MAC address on Windows, Linux and Apple Mac.
All network adapters have an unique identifier assigned by the manufacturer known as Media Access Control address (MAC address), this MAC address is used to identify a particular device on a network and was intended as a globally unique identification numbering system to trace network activity and implement restrictions and security, MAC address are used by many ISP's worldover for binding network access to a particular modem, however this MAC number can be changed easily via readily available noob friendly MAC spoofing tools, here are few tricks and tools to spoof your MAC address on Windows, Linux and Apple Mac.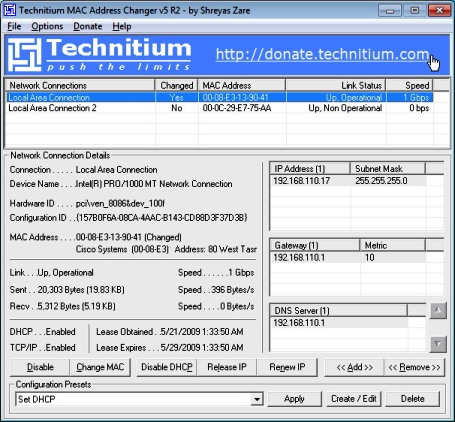
 Few days ago I posted the most easiest way to
Few days ago I posted the most easiest way to 