In past, researchers have found various XSS (cross-site scripting) vulnerabilities in Google services allowing hackers to gain un-authorized access to users accounts which are now patched, but in an entirely new type of "Frame Injection Vulnerability" found by Adrian Pastor of the GNUCitizen, the researcher displayed how attackers can create authentic-looking spoof pages meant to steal user login information, the exploit allows attackers to inject third-party content into Google pages bypassing phising filters.
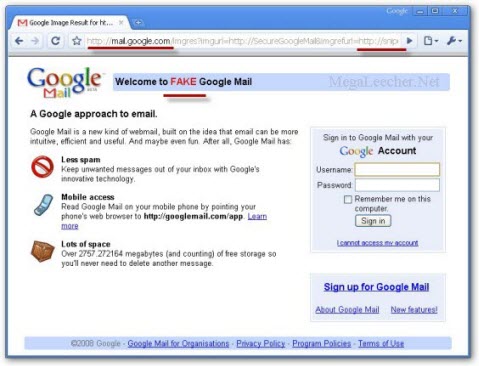
Adrian posted proof-of-concept (do not enter any login info here) of this new exploit allowing him to inject fake Gmail login frame inside Google pages hosted on mail.Google.com domain, the result page looks legitimate as the domain displayed in user address bar is mail.google.com increasing the hackers chances of getting the login data.
According to another security researcher Aviv Raff, Google's security problem lies into its design:
"Google.com suffers from a cross-domain web-application sharing security design flaw. There are several Google web applications which are accessible over multiple google.com subdomains. The following are some of those web-applications and subdomains:
* Google Maps (maps.google.com)
* Google Mail (mail.google.com)
* Google Images (images.google.com)
* Google News (news.google.com)
* Google.com (Google Search, Google Accounts, Google Apps, Google History, etc.)Here's example of Google News being hosted on the Google Maps subdomain:
http://maps.google.com/news?sa=N&tab=ln"
Comments
Google Redesigned
For Firefox users there are a couple of add-ons forcing Gmail to open in a secure (https://) way. Get them at the Add-on site. "Better Gmail 2" and "Better Gcal" for the Calendar, as well as "Google redesigned".
Google
"Google.com suffers from a cross-domain web-application sharing security design flaw. There are several Google web applications which are accessible over multiple google.com subdomains. The following are some of those web-applications and subdomains:
which are now patched, but
which are now patched, but in an entirely new type of "Frame Injection Vulnerability" found by Adrian Pastor of the GNUCitizen, the researcher displayed how attackers can create authentic-looking spoof pages meant to steal user login information, the exploit allows attackers to inject third-party content into Google pages bypassing phising filters.
Add new comment