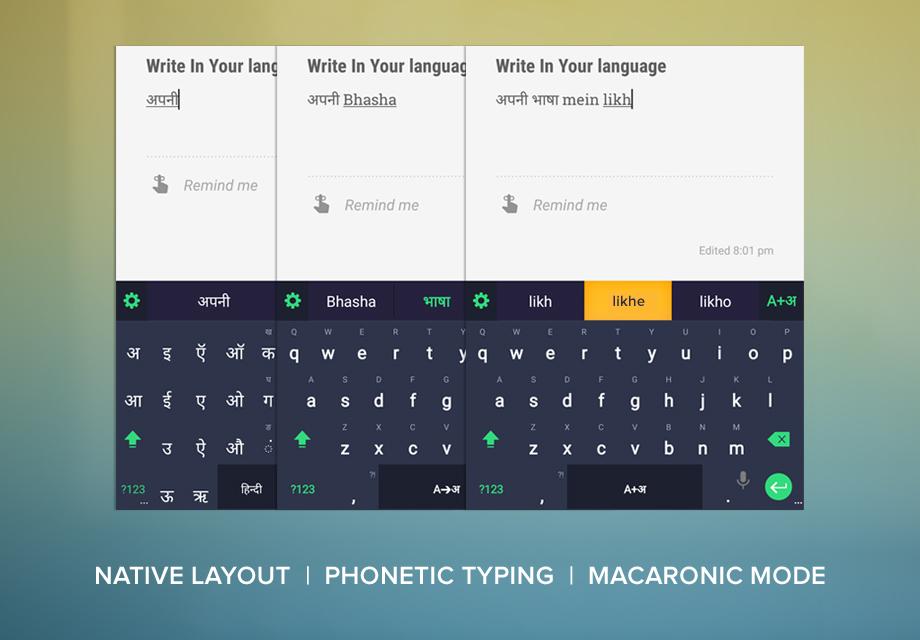
If you were looking for a solution for protected, secure and unlimited access to web sources, look no more. March 27th-28th,2015 are you lucky days to grab a month of VPN Unlimited subscription for absolutely FREE. Hurry to take advantage of the special 48-hour offer for our readers, go to https://www.vpnunlimitedapp.com/deals and get the service at no charge to you.
VPN Unlimited is a top-notch VPN service, ensuring your privacy, anonymity and Internet safety, with unlimited connection speed and no traffic bandwidth. When connecting to a public Wi-Fi hotspot, VPN Unlimited protects and encrypts the data you send and receive so no scam or hacker can use your personal information. When travelling and want to access your favorite, but geo-restricted, sources, the service helps you bypass some restrictions and stay anonymous. All your online activity is protected, i.e. no one can track it, when you connect to one of a number of solid servers in 22 regions all over the world. Better yet, every other week a new server in a new region becomes available for VPN Unlimited users.

Online shopping and booking tickets are more convenient with VPN Unlimited too. You must have heard that airfares could vary depending on location and even on the number of times you checked the offer. The more you look for the most affordable price, the higher it shows up for you. But if you use VPN Unlimited, thus change your IP address and choose the location you want, rest assured the prices you see are the cheapest.


 In earlier days of Google Android OS, one has to root and hack their way into the core operating-system files just to
In earlier days of Google Android OS, one has to root and hack their way into the core operating-system files just to